Patterns
At the heart of surveilr is the flexibility to adapt to a wide range of industries, disciplines, and use cases. This adaptability is enabled through a combination of the surveilr Core engine and a modular approach to Patterns.
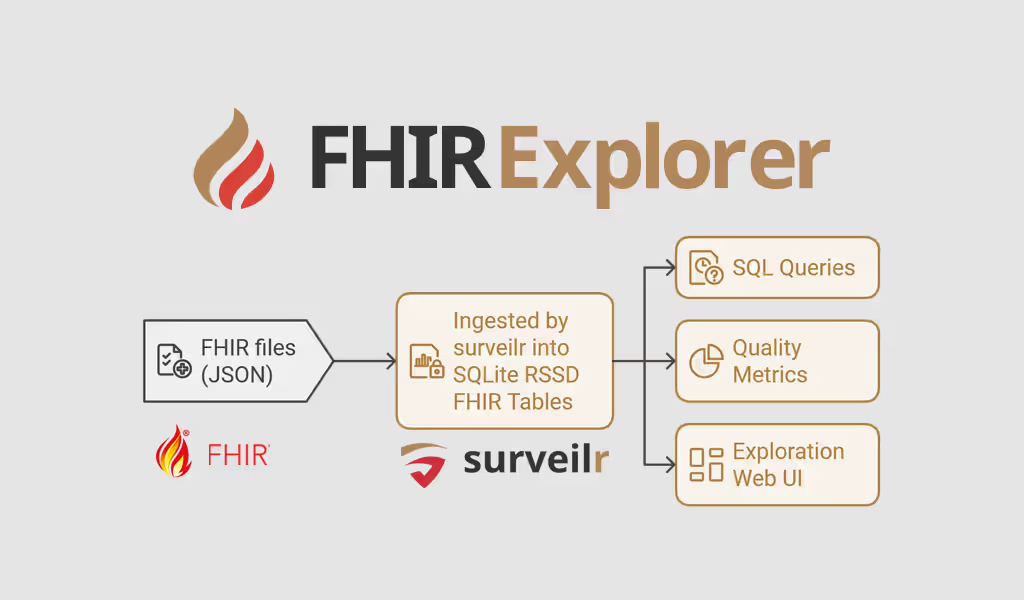 HL7 FHIR Content Aggregator and Explorer
HL7 FHIR Content Aggregator and Explorer 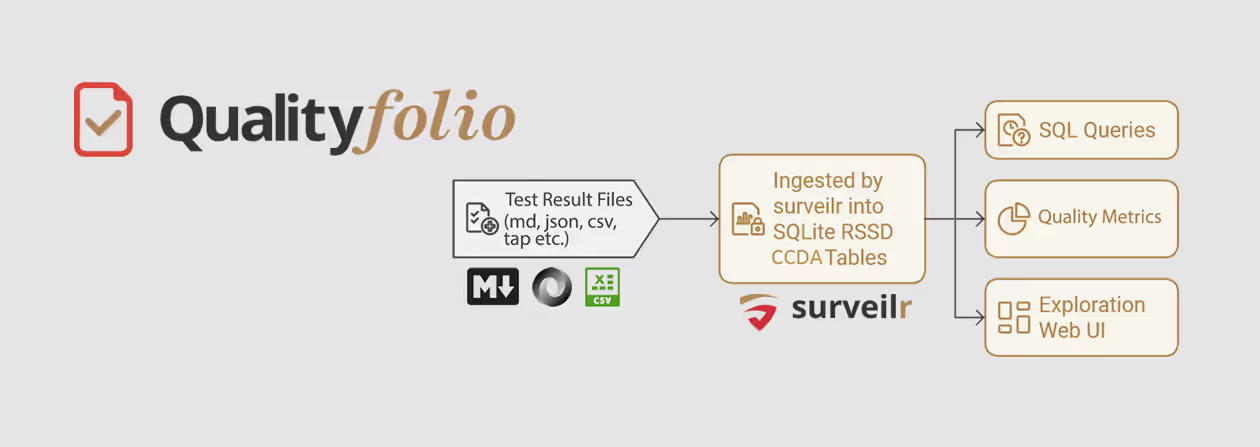 Unified Test and Quality Management System
Unified Test and Quality Management System 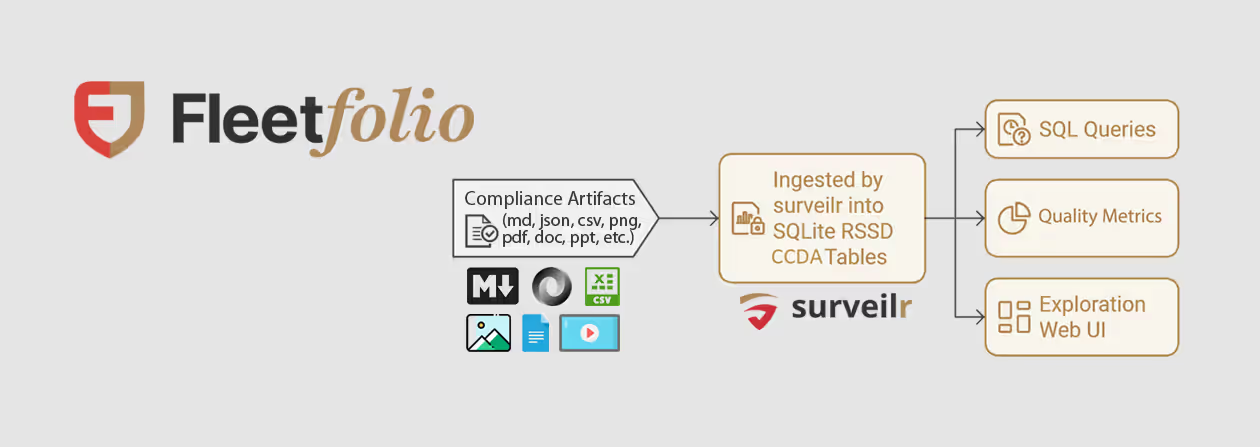 Continuous Asset and Identity Intelligence for Enhanced Security
Continuous Asset and Identity Intelligence for Enhanced Security 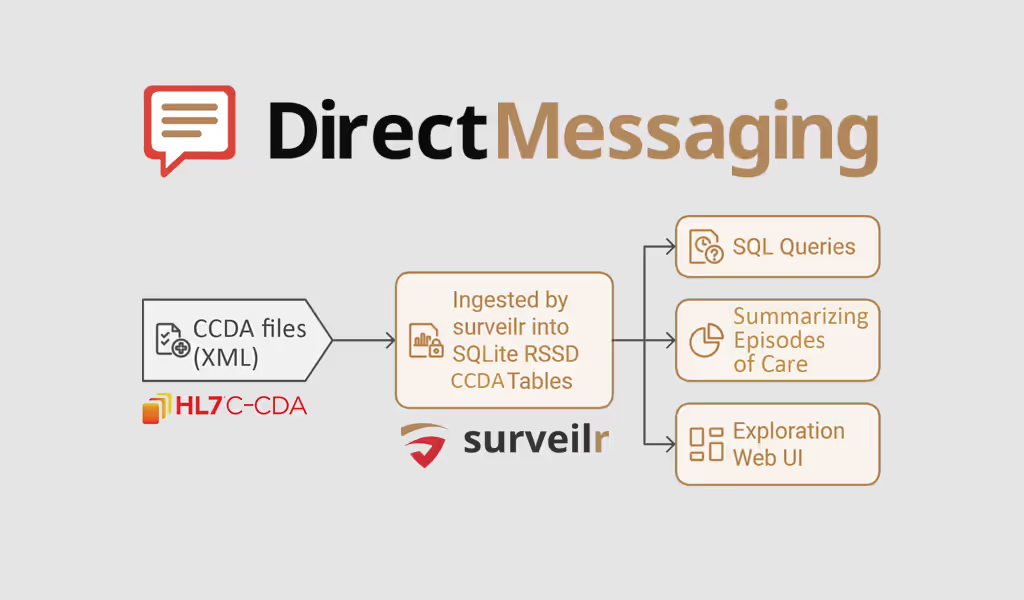 Trusted and protected health information exchange is backed by the Direct Standard®
Trusted and protected health information exchange is backed by the Direct Standard® 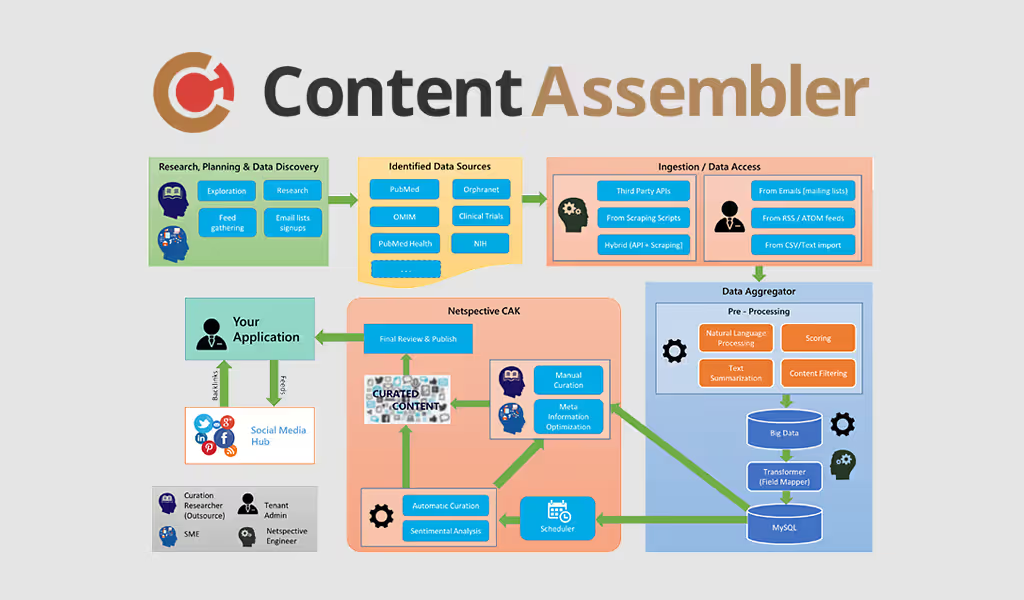 Content curation, assembly, and distribution platform
Content curation, assembly, and distribution platform 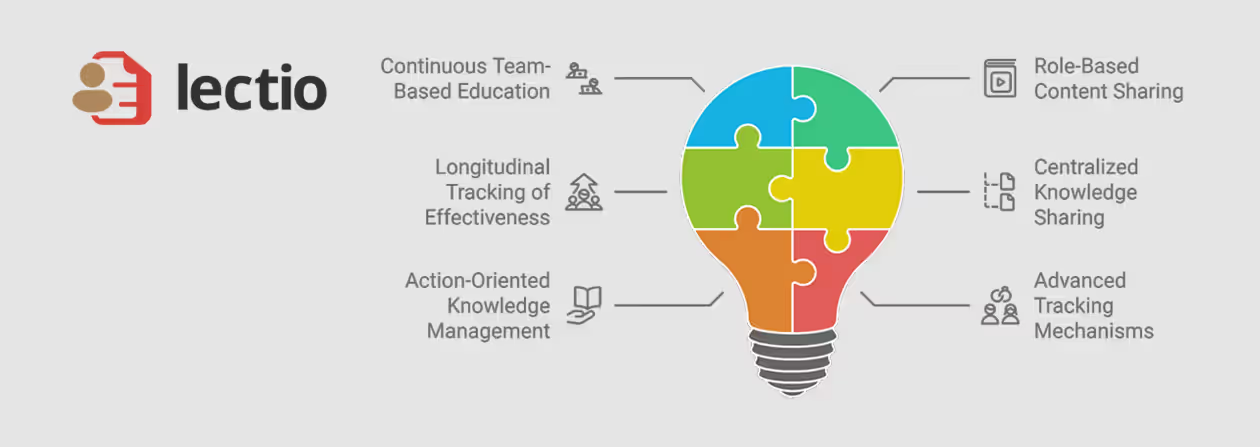 Team-based reading assignment and content collaboration solution
Team-based reading assignment and content collaboration solution 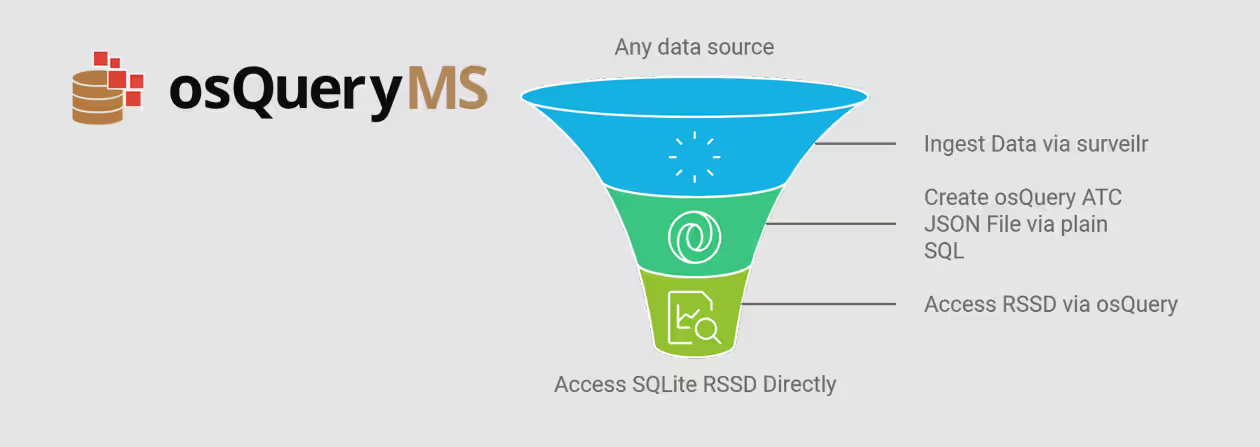 Surface surveilr RSSD tables via osQuery
Surface surveilr RSSD tables via osQuery 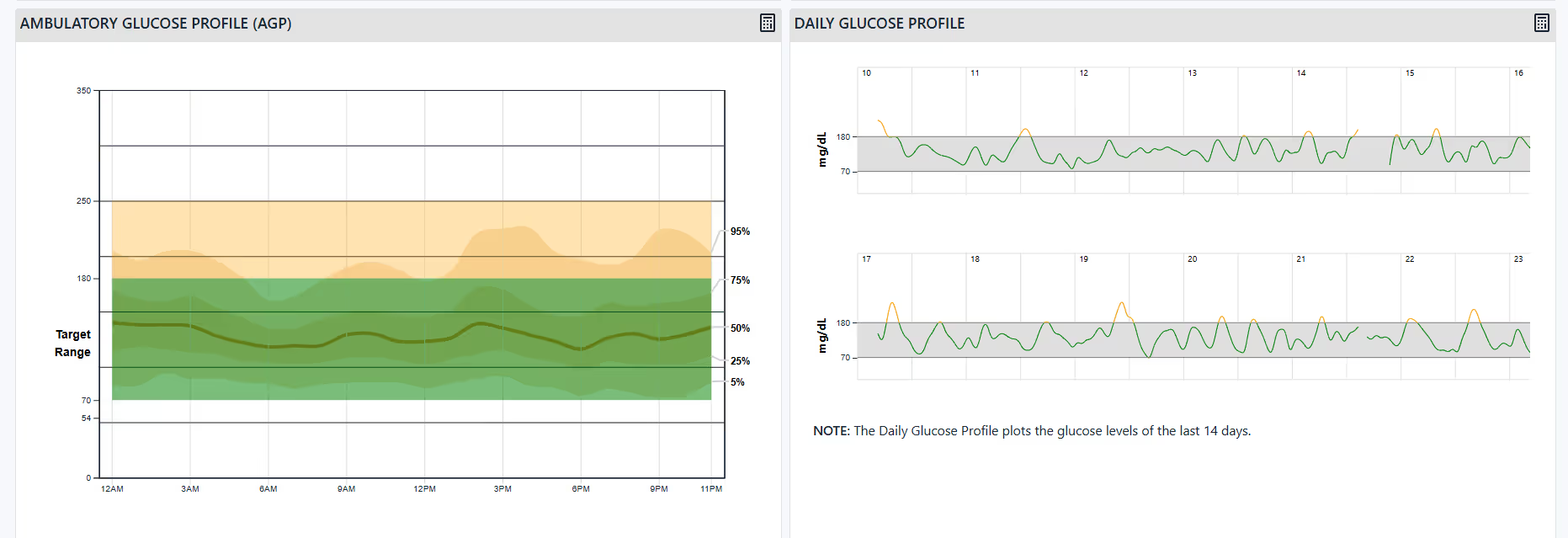 A seamless integration for converting study files and generating metrics, visual insights for diabetes research.
A seamless integration for converting study files and generating metrics, visual insights for diabetes research. 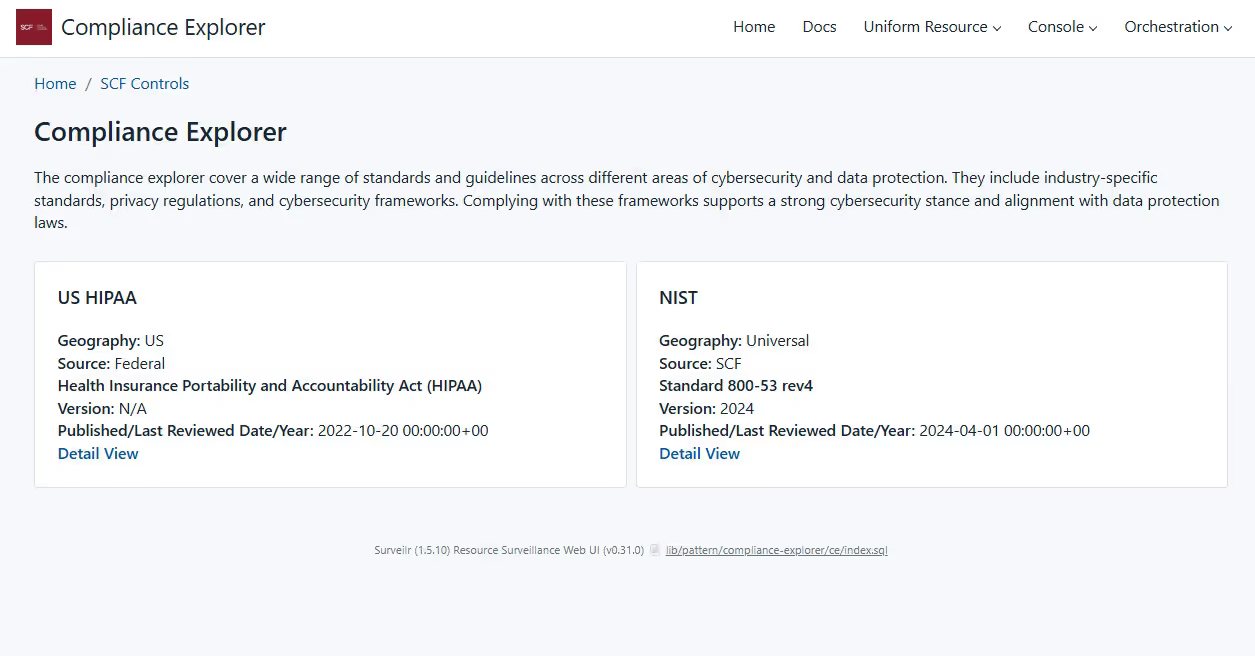 Web-based user interface that lists and displays SCF controls Aggregator and Explorer
Web-based user interface that lists and displays SCF controls Aggregator and Explorer 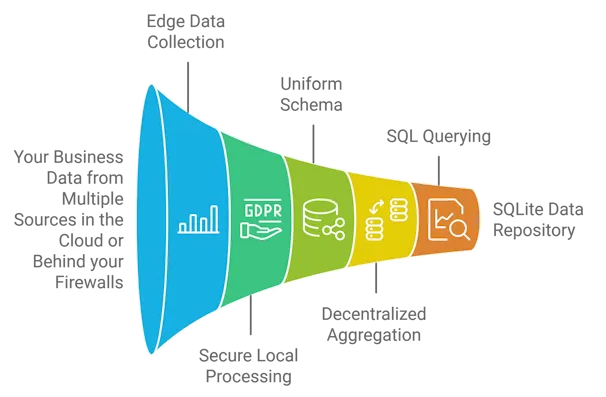
Why use surveilr patterns?
Don't rely on humans for evidence, use surveilr patterns to help acquire, collect, integrate, and query evidence in a secure warehouse.
- Robust and reliable solutions that securely run in your environment.
- Innovative solutions tailored to modern compliance needs.
- Customer support dedicated to your project's success.
What Our Customers Say
"Since implementing surveilr and its FHIR Explorer Pattern, we’ve drastically reduced the time it takes to audit our healthcare data. The ability to query and explore FHIR files without needing a technical team has been a game-changer for us. We can now ensure compliance and data accuracy with minimal effort."

Dr. Emily Harper
Chief Medical Information Officer | Medisync Health Systems
"As a financial services company, maintaining regulatory compliance across multiple systems was a major challenge. With surveilr, we now have a streamlined solution that provides automated compliance reports, auditable evidence, and real-time insights, all while minimizing our need for IT support."

James Chen
Compliance Director | Argent Financial Solutions
"Our cybersecurity team has benefited immensely from using surveilr to monitor and audit our security logs. The automatic generation of machine-attestable evidence has not only improved our compliance efforts but also helped us quickly respond to incidents with confidence."

Richard Kim
Chief Information Security Officer | NetSecure Technologies